- OCSP 知识请自行查阅相关资料,此处不做过多解释
- 发送OCSP请求前提:得到用户证书、证书链;所以文章前半部分是关于如何获取数字证书以及对应的证书链教程,如果你已经有这部分数据,请自行跳过。
准备工作
获取证书
方式一
自行从供应商处下载证书
方式二
如果是在线网站,可通过如下命令得到证书,如获取 www.eamonzhang.com 网站证书
# 保存到 eamonzhang.pem 中
openssl s_client -connect eamonzhang.com:443 2>&1 < /dev/null | sed -n '/-----BEGIN/,/-------END/p' > eamonzhang.pem
获取证书链
方式一
通过解析证书中的ICA地址,手动下载:
# 执行如下命令得到证书详情信息
openssl x509 -text -noout -in eamonzhang.pem
结果如下:
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
04:59:ea:99:fa:e4:76:43:ec:06:54:3c:f6:45:53:e0:4f:e5
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=US, O=Let's Encrypt, CN=R3
Validity
Not Before: Feb 16 13:02:05 2022 GMT
Not After : May 17 13:02:04 2022 GMT
Subject: CN=eamonzhang.com
Subject Public Key Info:
Public Key Algorithm: id-ecPublicKey
Public-Key: (384 bit)
pub:
04:88:e9:52:33:af:1f:2a:e7:a6:5f:a0:3f:24:fb:
...
ASN1 OID: secp384r1
NIST CURVE: P-384
X509v3 extensions:
X509v3 Key Usage: critical
Digital Signature
X509v3 Extended Key Usage:
TLS Web Server Authentication, TLS Web Client Authentication
X509v3 Basic Constraints: critical
CA:FALSE
X509v3 Subject Key Identifier:
D9:D0:13:D4:05:4E:DB:0D:E0:87:E5:9A:E5:B4:81:9E:21:2D:9C:99
X509v3 Authority Key Identifier:
keyid:14:2E:B3:17:B7:58:56:CB:AE:50:09:40:E6:1F:AF:9D:8B:14:C2:C6
Authority Information Access:
OCSP - URI:http://r3.o.lencr.org
CA Issuers - URI:http://r3.i.lencr.org/
X509v3 Subject Alternative Name:
DNS:*.eamonzhang.com, DNS:eamonzhang.com
X509v3 Certificate Policies:
Policy: 2.23.140.1.2.1
Policy: 1.3.6.1.4.1.44947.1.1.1
CPS: http://cps.letsencrypt.org
1.3.6.1.4.1.11129.2.4.2:
......v...^.h.O.l..._N>Z.....j^.;.. D\*s.............G0E. l.3;[5....ey.....uu.iy..4..KM.I..!....t.~..|$~..ui.k..@.k}...T......u.F.U.u.. 0...i..}.,At..I.....p.mG.............F0D. I...ME..dV....%..S.....qI.
,Q..Y. s..f.x..C.F...O..9.s..U.*..lE.2I
Signature Algorithm: sha256WithRSAEncryption
9d:5d:c0:0f:0b:bc:f1:19:2a:a6:85:64:42:52:76:69:d7:0c:
...
在详细信息中找到如下内容:
Authority Information Access:
OCSP - URI:http://r3.o.lencr.org
CA Issuers - URI:http://r3.i.lencr.org/
其中 CA Issuers - URI:所对应的即为CA下载地址,手动访问该地址即可得到上级CA的证书,然后再解析上级CA证书信息,知道得到RootCA证书即可。
方式二
如果是在线网站,则通过如下方式可快速获取(利用 openssl s_client -showcerts):
# 得到完整证书链,输出内容包含用户证书和CA证书
openssl s_client -connect eamonzhang.com:443 -showcerts 2>&1 < /dev/null
结果部分内容如下(内容过长,部分内容已省略):
CONNECTED(00000005)
depth=2 C = US, O = Internet Security Research Group, CN = ISRG Root X1
verify return:1
depth=1 C = US, O = Let's Encrypt, CN = R3
verify return:1
depth=0 CN = eamonzhang.com
verify return:1
---
Certificate chain
0 s:/CN=eamonzhang.com
i:/C=US/O=Let's Encrypt/CN=R3
-----BEGIN CERTIFICATE-----
MIIEhTCCA22gAwIBAgISBFnqmfrkdkPsBlQ89kVT4E/lMA0GCSqGSIb3DQEBCwUA
MDIxCzAJBgNVBAYTAlVTMRYwFAYDVQQKEw1MZXQncyBFbmNyeXB0MQswCQYDVQQD
........
-----END CERTIFICATE-----
1 s:/C=US/O=Let's Encrypt/CN=R3
i:/C=US/O=Internet Security Research Group/CN=ISRG Root X1
-----BEGIN CERTIFICATE-----
MIIFFjCCAv6gAwIBAgIRAJErCErPDBinU/bWLiWnX1owDQYJKoZIhvcNAQELBQAw
TzELMAkGA1UEBhMCVVMxKTAnBgNVBAoTIEludGVybmV0IFNlY3VyaXR5IFJlc2Vh
........
-----END CERTIFICATE-----
2 s:/C=US/O=Internet Security Research Group/CN=ISRG Root X1
i:/O=Digital Signature Trust Co./CN=DST Root CA X3
-----BEGIN CERTIFICATE-----
MIIFYDCCBEigAwIBAgIQQAF3ITfU6UK47naqPGQKtzANBgkqhkiG9w0BAQsFADA/
MSQwIgYDVQQKExtEaWdpdGFsIFNpZ25hdHVyZSBUcnVzdCBDby4xFzAVBgNVBAMT
DkRTVCBSb290IENBIFgzMB4XDTIxMDEyMDE5MTQwM1oXDTI0MDkzMDE4MTQw......
-----END CERTIFICATE-----
......
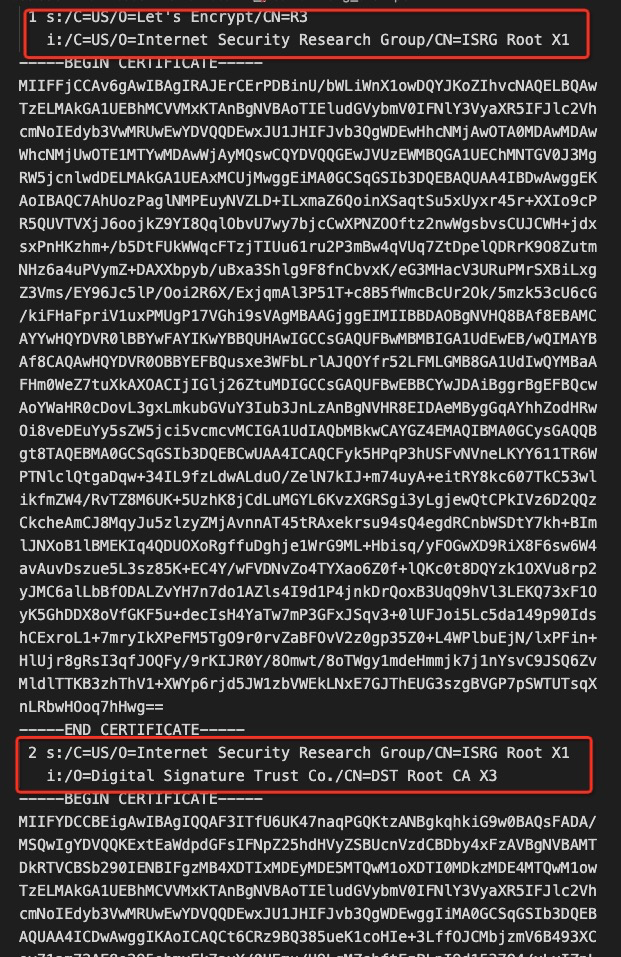
1 s:/C=US/O=Let's Encrypt/CN=R3 内容段落表示eamonzhang.com 的上级CA证书(也叫中级CA证书);
2 s:/C=US/O=Internet Security Research Group/CN=ISRG Root X1 内容段落表示根CA证书
依次将该段的内容保存到文件中即可,如 eamonzhang_chain.pem
如图:
注意: 某些证书发行商可能会存在3级或多级证书链,全部保存即可
获取 OCSP 地址
方式一
直接查看证书详情获取
方式二
使用 OpenSSL 提取
openssl x509 -noout -ocsp_uri -in eamonzhang.pem
得到类似于:http://r3.o.lencr.org 的地址(如果没有,请通过其他渠道进行获取,本文章不提供解决方案)
发送 OCSP 请求
POST方式
方式一
直接使用 OpenSSL 发送OCSP请求即可:
# text 是显示详情参数,如果不想看OCSP的请求和响应详情,可删除该参数,可选
# VAfile 是用作验证结果的参数(解决输出中证书验证失败问题),可选
# issuer 签发者,可以是中级CA,这里直接使用完整证书链即可,必须
# cert 待验证的证书
# url OCSP 地址
# header 为解决某些情况下出现类似于 OCSP routines:PARSE_HTTP_LINE1 报错时,可添加该参数解决
openssl ocsp -text -VAfile eamonzhang_chain.pem -issuer eamonzhang_chain.pem -cert eamonzhang.pem -url http://r3.o.lencr.org -header 'host' 'r3.o.lencr.org'
得到的内容大致如下:
OCSP Request Data:
Version: 1 (0x0)
Requestor List:
Certificate ID:
Hash Algorithm: sha1
Issuer Name Hash: 48DAC9A0FB2BD32D4FF0DE68D2F567B735F9B3C4
Issuer Key Hash: 142EB317B75856CBAE500940E61FAF9D8B14C2C6
Serial Number: 0459EA99FAE47643EC06543CF64553E04FE5
Request Extensions:
OCSP Nonce:
041086F9470DCA2E293790BF85538E459430
OCSP Response Data:
OCSP Response Status: successful (0x0)
Response Type: Basic OCSP Response
Version: 1 (0x0)
Responder Id: C = US, O = Let's Encrypt, CN = R3
Produced At: Apr 12 14:02:00 2022 GMT
Responses:
Certificate ID:
Hash Algorithm: sha1
Issuer Name Hash: 48DAC9A0FB2BD32D4FF0DE68D2F567B735F9B3C4
Issuer Key Hash: 142EB317B75856CBAE500940E61FAF9D8B14C2C6
Serial Number: 0459EA99FAE47643EC06543CF64553E04FE5
Cert Status: good
This Update: Apr 12 14:00:00 2022 GMT
Next Update: Apr 19 13:59:58 2022 GMT
Signature Algorithm: sha256WithRSAEncryption
a1:c3:b1:13:de:3c:3b:51:b5:f1:c3:01:a0:7e:50:8d:d6:16:
c5:3a:04:46:5d:01:16:3b:8a:a3:24:08:ec:0b:e2:f1:e0:ca:
f5:45:b0:fd:6a:39:4f:8b:7b:b7:04:18:aa:40:01:32:0b:b2:
83:5f:e2:fd:39:37:36:32:37:57:9a:d2:92:50:72:21:eb:1b:
......
WARNING: no nonce in response
Response verify OK
eamonzhang.pem: good
This Update: Apr 12 14:00:00 2022 GMT
Next Update: Apr 19 13:59:58 2022 GMT
方式二
使用 curl 工具:
- 创建 OCSP 请求数据
# 利用 openssl 构建请求文件,得到 ocsp.req 请求文件
openssl ocsp -text -VAfile eamonzhang_chain.pem -issuer eamonzhang_chain.pem -cert eamonzhang.pem -reqout ocsp.req
内容如下:
OCSP Request Data:
Version: 1 (0x0)
Requestor List:
Certificate ID:
Hash Algorithm: sha1
Issuer Name Hash: 48DAC9A0FB2BD32D4FF0DE68D2F567B735F9B3C4
Issuer Key Hash: 142EB317B75856CBAE500940E61FAF9D8B14C2C6
Serial Number: 0459EA99FAE47643EC06543CF64553E04FE5
Request Extensions:
OCSP Nonce:
04103F241E7F2F78FAFEAC10AED4A92EA5DE
- 使用
curl工具发送OCSP请求,得到ocsp.rep响应文件
# -v 显示详情
# -o 输出位置
# --data-binary 添加请求体数据文件(ocsp request 数据)
# -H 添加请求头,OCSP 请求的请求内容类型Content-Type必须为application/ocsp-request
# url OCSP地址
curl -v -o ocsp.rep --data-binary @ocsp.req -H "Content-Type: application/ocsp-request" --url http://r3.o.lencr.org
- 解析响应
# -noverify 代表不验证响应签名,如果需要的话,自行添加 -VAfile 参数指定签发者CA来验证
openssl ocsp -text -respin ocsp.rep -noverify
得到结果如下:
OCSP Response Data:
OCSP Response Status: successful (0x0)
Response Type: Basic OCSP Response
Version: 1 (0x0)
Responder Id: C = US, O = Let's Encrypt, CN = R3
Produced At: Apr 12 14:02:00 2022 GMT
Responses:
Certificate ID:
Hash Algorithm: sha1
Issuer Name Hash: 48DAC9A0FB2BD32D4FF0DE68D2F567B735F9B3C4
Issuer Key Hash: 142EB317B75856CBAE500940E61FAF9D8B14C2C6
Serial Number: 0459EA99FAE47643EC06543CF64553E04FE5
Cert Status: good
This Update: Apr 12 14:00:00 2022 GMT
Next Update: Apr 19 13:59:58 2022 GMT
Signature Algorithm: sha256WithRSAEncryption
a1:c3:b1:13:de:3c:3b:51:b5:f1:c3:01:a0:7e:50:8d:d6:16:
c5:3a:04:46:5d:01:16:3b:8a:a3:24:08:ec:0b:e2:f1:e0:ca:
......
GET 方式
- 构建
OCSP Request数据
openssl ocsp -text -VAfile eamonzhang_chain.pem -issuer eamonzhang_chain.pem -cert eamonzhang.pem -reqout ocsp.req
- 将
OCSP Request数据进行Base64编码
# Base64 加密
# -A 得到的结果不换行
openssl enc -in ocsp.req -out ocsp.req.b64 -a -A
- 将编码后的数据拼接道
OCSP Url中,并执行请求
curl -v -o ocsp.rep --url http://r3.o.lencr.org/`{cat ocsp.req.b64}`
- 解析响应数据
openssl ocsp -text -respin ocsp.rep -noverify
得到结果如下:
OCSP Response Data:
OCSP Response Status: successful (0x0)
Response Type: Basic OCSP Response
Version: 1 (0x0)
Responder Id: C = US, O = Let's Encrypt, CN = R3
Produced At: Apr 12 14:02:00 2022 GMT
Responses:
Certificate ID:
Hash Algorithm: sha1
Issuer Name Hash: 48DAC9A0FB2BD32D4FF0DE68D2F567B735F9B3C4
Issuer Key Hash: 142EB317B75856CBAE500940E61FAF9D8B14C2C6
Serial Number: 0459EA99FAE47643EC06543CF64553E04FE5
Cert Status: good
This Update: Apr 12 14:00:00 2022 GMT
Next Update: Apr 19 13:59:58 2022 GMT
Signature Algorithm: sha256WithRSAEncryption
a1:c3:b1:13:de:3c:3b:51:b5:f1:c3:01:a0:7e:50:8d:d6:16:
c5:3a:04:46:5d:01:16:3b:8a:a3:24:08:ec:0b:e2:f1:e0:ca:
f5:45:b0:fd:6a:39:4f:8b:7b:b7:04:18:aa:40:01:32:0b:b2:
83:5f:e2:fd:39:37:36:32:37:57:9a:d2:92:50:72:21:eb:1b:
86:b5:2b:6b:e2:52:32:3f:36:70:14:84:44:25:8f:43:56:4b:
c9:67:58:c3:22:01:65:7e:75:70:88:94:b9:2b:dc:44:a5:26:
......
至此,GET 与 POST 请求方式请求 OCSP 检查证书状态结束,如有任何问题,欢迎提出,互相学习!!!


评论区